Verci Spy System
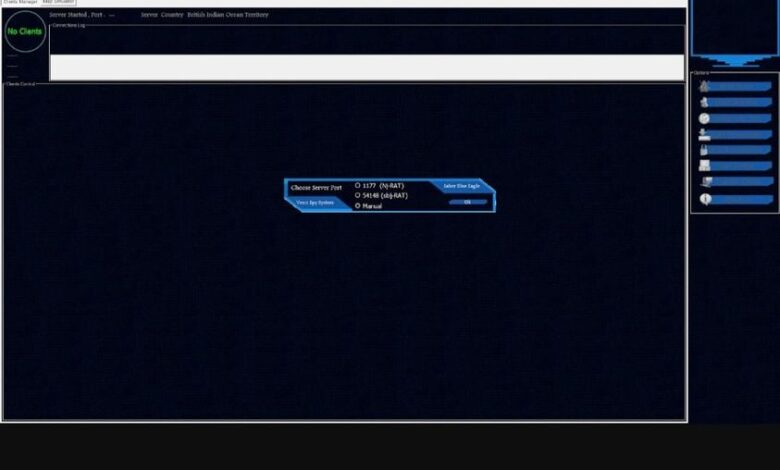
he Verci Spy System is a Remote Access Trojan (RAT) that offers a comprehensive suite of tools for remote control and surveillance. It is marketed as a powerful and versatile system with various features that make it suitable for both legal and illegal activities, though it is officially claimed to be for educational purposes only.
Key Features of Verci Spy System:
1. Remote Control Capabilities:
Remote Desktop: Control and monitor the desktop environment of the target machine.
Disk Manager: Access and manage the disk drives remotely.
Remote Clipboard: View and manage clipboard content on the target machine.
2. Device and Network Management:
– Remote Process Manager: Manage running processes on the target system.
– Network Card Manager: Control network adapters and manage LAN settings.
– Wi-Fi Control: Manage and control Wi-Fi settings remotely.
– Remote LAN Management: Oversee and manage local network settings and devices.
3. System Monitoring and Control:
– Keylogging: Capture keystrokes from the target device.
– password Stealing: Extract saved passwords from the target system.
– HTTP DDoS: Launch distributed denial-of-service attacks.
– Client Information Retrieval: Gather detailed information about the client system.
4. Additional Tools and Features:
– Ransomware Module: Encrypt files on the target system and demand ransom.
– Remote Command Prompt: Execute commands on the target system via the command line.
– Media Devices Control: Manage and control media devices connected to the target.
– Remote Code Compiler: Compile and run code remotely on the target system.
– Spam Tool: Send spam emails from the target machine.
– Remote Chat: Open a chat with the target user.
5. File and System Access:
– File Execution: Run files on the target system.
– URL Opening: Force the target system to open specific URLs.
– Backdoor Options: Maintain persistent access to the target system even after the initial compromise.
6. User Interface and Management:
– Remote Regedit: Edit the registry of the target system remotely.
– Remote Installed Programs; Manager View and manage installed programs on the target system.
– Open-Source Availability: The source code is available for educational purposes, allowing for modifications and customizations【12†source】【13†source】【14†source】.
This system is a high-risk tool that can be used for malicious activities, and its use is illegal in many jurisdictions when used without proper authorization.