Zero Trust Architecture: The Next Standard for Enterprise Security?
What is Zero Trust Architecture?
Zero Trust Architecture (ZTA) is a security model that assumes no one, inside or outside a network, should be trusted automatically. Instead, it treats every access request as potentially harmful. Traditional security models focus on securing a perimeter. They rely on the idea that anyone within this perimeter is trustworthy. But with Zero Trust, all users and devices must prove their identity and authorization repeatedly, no matter where they are.
Zero Trust has gained popularity as cyber threats evolve. The rise of remote work and cloud-based services has blurred the boundaries of networks. This model has emerged as a powerful response, offering a robust defense against modern cyber threats.
Why is Zero Trust Important in Cybersecurity?
The Zero Trust approach responds to weaknesses in traditional security models. As organizations grow and adopt new technologies, their networks expand. They now have multiple devices, users, and systems connected at all times. Cybercriminals can exploit any vulnerable entry point. If they bypass the perimeter, they can easily access sensitive data.
With Zero Trust, even if a hacker manages to enter a network, they cannot move freely. Zero Trust divides the network into small, secure segments. Each segment requires strict authentication and access controls. This approach limits an attacker’s ability to access data or disrupt systems.

How Does Zero Trust Work?
Zero Trust involves several key principles to ensure security. These include continuous verification, least-privilege access, and segmentation.
- Continuous Verification: Zero Trust requires users to verify their identity continuously. Verification doesn’t happen just once, such as at login. It is an ongoing process, checking user identity, device status, and other factors at regular intervals. This reduces the chance of unauthorized access over time.
- Least-Privilege Access: In Zero Trust, users and devices receive only the minimum permissions needed. This “least-privilege” approach restricts access to essential resources only. By limiting access, Zero Trust reduces potential damage if an account is compromised.
- Network Segmentation: Zero Trust divides the network into small, isolated segments. Each segment has its own access controls and security policies. This segmentation limits the movement of attackers within the network. If an attacker gains access to one segment, they cannot reach other areas without further authentication.
These principles make Zero Trust Architecture adaptable. It can fit organizations of all sizes, from small businesses to large enterprises.
Benefits of Zero Trust for Enterprises
Zero Trust offers multiple benefits for enterprise security. Here are a few key advantages:
- Enhanced Security: By assuming no trust, Zero Trust reduces the risk of data breaches. It constantly verifies every user, device, and application that requests access. This approach minimizes the potential for unauthorized access.
- Improved Control: Zero Trust provides greater control over user and device activity. Enterprises can monitor network traffic and detect suspicious actions quickly. This allows them to respond to threats in real-time, reducing the impact of any breach.
- Better Compliance: Many regulations require strict data protection practices. Zero Trust helps organizations meet these compliance requirements. It limits access to sensitive data and keeps a record of access requests. This is especially useful for industries with strict data protection standards, like healthcare and finance.
- Simplified Security Management: Zero Trust Architecture can simplify security management for enterprises. Since it operates on a unified set of security rules, organizations can manage policies and access controls in one place. This centralization saves time and resources, especially for IT teams.
Challenges in Implementing Zero Trust Architecture
Despite its benefits, Zero Trust comes with some challenges. Implementing it across an enterprise requires planning, resources, and commitment. Below are some common challenges:
- Complexity: Zero Trust involves multiple components, from identity verification to segmentation. Integrating these with existing systems can be complex. Organizations may need to upgrade their infrastructure to support Zero Trust policies effectively.
- Cost: Implementing Zero Trust requires investment in technology, training, and resources. Small to medium-sized businesses might find the cost a barrier. However, many security experts argue that the long-term benefits outweigh the initial investment.
- Cultural Shift: Zero Trust requires a change in mindset. Employees may resist the frequent verification processes, viewing them as inconvenient. Organizations need to educate staff on the importance of Zero Trust and why it’s necessary.
- Data and Privacy Concerns: Zero Trust relies on monitoring user behavior and tracking access. This might raise concerns about data privacy. Organizations need to handle data responsibly and communicate their policies clearly.
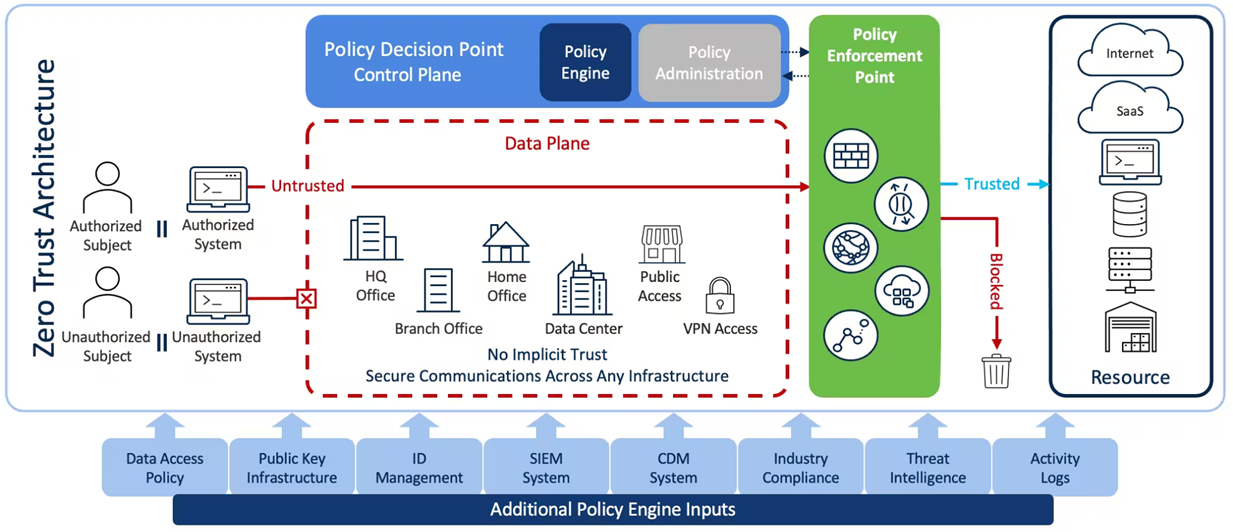
Key Components of a Zero Trust Strategy
Building a Zero Trust framework involves several key elements. Here’s a look at the main components:
- Identity and Access Management (IAM): IAM systems manage user identities and control access. These systems verify user identities before granting access to resources. They are essential for applying least-privilege access policies.
- Multi-Factor Authentication (MFA): MFA adds an extra layer of security. It requires users to verify their identity through multiple factors, such as passwords, fingerprints, or authentication apps. MFA makes it harder for attackers to access sensitive data.
- Endpoint Security: Zero Trust requires security for all devices connected to the network. Endpoint security tools monitor device health and protect against malware or other threats. They ensure that only secure devices access the network.
- Micro-Segmentation: Micro-segmentation divides the network into smaller segments. Each segment has specific access rules, making it difficult for attackers to move across the network. Micro-segmentation enhances security by isolating threats.
- Data Encryption: Encrypting data ensures that sensitive information stays protected, even if accessed by unauthorized users. Data encryption plays a key role in Zero Trust by securing data at rest and in transit.
- Continuous Monitoring and Analytics: Zero Trust relies on continuous monitoring to detect potential threats. Analytics help identify unusual behavior or patterns that indicate risks. By monitoring in real-time, organizations can respond to threats quickly.
The Future of Zero Trust in Enterprise Security
Zero Trust is gaining traction across industries. With rising cyber threats, more organizations see the need for a stronger security model. The flexibility of Zero Trust makes it suitable for a variety of industries, from finance to healthcare.
Moreover, as more companies embrace remote work, the need for secure, adaptable networks grows. Zero Trust offers a way to protect remote employees and cloud-based resources. It can secure users regardless of their physical location, a crucial advantage in today’s digital landscape.
As technology advances, Zero Trust may integrate with AI and machine learning. These technologies could make continuous monitoring more effective, helping organizations detect threats faster. The combination of AI and Zero Trust could lead to even stronger security measures.
Conclusion: Is Zero Trust the New Standard for Enterprise Security?
Zero Trust Architecture is emerging as a new standard in cybersecurity. By challenging the assumption of trust, it offers stronger defenses against modern threats. Organizations implementing Zero Trust can achieve higher security, control, and compliance.
Despite challenges, the benefits of Zero Trust make it a worthwhile investment. Its principles align well with the demands of today’s digital environment. As cybersecurity threats evolve, Zero Trust offers a proactive approach. For enterprises, it’s a step toward a more resilient and secure future.
Zero Trust might not replace traditional security models entirely, but it’s a strong addition. By focusing on identity verification, least-privilege access, and continuous monitoring, it’s well-suited for the modern enterprise. As more organizations adopt Zero Trust, it could become the new gold standard in enterprise security.




